Microsoft New Released Exam 70-342 exam questions are now can be download from GreatExam! All 231 questions and answers are the latest! 100% exam pass guarantee! Get this IT exam certification in a short time!
QUESTION 1
You have an Exchange Server organization that contains five servers.
The servers are configured as shown in the following table.
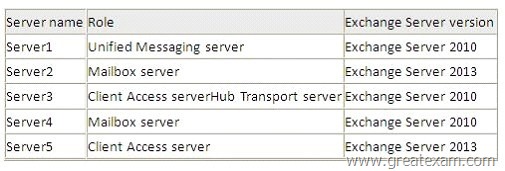
You deploy Microsoft Lync Server 2010.
You need to create a Lync Server SIP Unified Messaging (UM) dial plan to enable voice integration between Lync Server and Exchange Server.
Which three Exchange servers should you associate to the UM dial plans? (Each correct answer presents part of the solution. Choose three.)
A. Server1
B. Server2
C. Server3
D. Server4
E. Server5
Answer: ABE
Explanation:
A: You can enable Unified Messaging (UM) in Microsoft Exchange Server 2010.
You must enable the Exchange computer running the Unified Messaging server role before the Unified Messaging server can process calls for UM-enabled Exchange 2010 recipients in your Exchange organization.
However, the Unified Messaging server also must be added to a UM dial plan before it can process calls for Unified Messaging.
BE:
* Requirements and Recommendations
Client Access and Mailbox. In Microsoft Exchange Server 2013, Exchange UM runs as a service on these servers.
* Deploy the Exchange Mailbox server roles in each Exchange Unified Messaging (UM) forest where you want to enable users for Exchange UM.
Reference: Configuring Unified Messaging on Microsoft Exchange Server to Work with Lync Server 2013
QUESTION 2
You have an Exchange Server 2013 organization.
All user mailboxes have an In-Place Archive enabled.
You need to identify which email message types can be archived by using a retention policy. Which message type or types should you identify? (Each correct answer presents part of the solution. Choose all that apply.)
A. calendar items
B. mail items
C. note items
D. task items
E. contact items
Answer: ABCD
Explanation:
Retention policy tags can created for these Folders:
* Calendar
This default folder is used to store meetings and appointments.
* Inbox
This default folder is used to store messages delivered to a mailbox.
* Notes
This folder contains notes created by users in Outlook.
These notes are also visible in Outlook Web App.
* Tasks
This default folder is used to store tasks.
Etc.
: Retention tags and retention policies
http://technet.microsoft.com/en-us/library/dd297955%28v=exchg.150%29.aspx
QUESTION 3
You plan to deploy 20 Client Access servers that will have Exchange Server 2013 installed.
You need to prepare the certificate required for the planned deployment. The solution must ensure that the same certificate can be used on all of the Client Access servers.
What should you do first?
A. From the Exchange Admin Center, create a new certificate request.
B. On each Client Access server, start the Certificates console and run the Certificate Import Wizard.
C. On all of the Client Access servers, delete the default self-signed certificates.
D. On one of the Client Access servers, run the Remove-ExchangeCertificate cmdlet.
Answer: A
Explanation:
You can use the EAC to generate certificate requests that work with most certificate issuers.
Note:
To prevent clients from receiving errors regarding untrusted certificates, the certificate that’s used by your Exchange server must be issued by someone that the client trusts. Although most clients can be configured to trust any certificate or certificate issuer, it’s simpler to use a trusted third-party certificate on your Exchange server. This is because most clients already trust their root certificates. There are several third-party certificate issuers that offer certificates configured specifically for Exchange.
QUESTION 4
Your company has an Exchange Server 2013 organization named adatum.com.
You purchase an Office 365 subscription and configure a hybrid deployment.
All recipients have an email address that contains a SMTP suffix of adatum.com.
You discover that all of the email messages sent to the Internet from users who have Office 365 mailboxes are routed through the on-premises Exchange servers.
You need to ensure that all of the email messages are sent directly to the Internet.
What should you do?
A. Modify the Send connector.
B. Run the Hybrid Configuration wizard.
C. Create a new Sharing policy.
D. Modify an organization relationship.
Answer: B
Explanation:
Creating and configuring a hybrid deployment with the Hybrid Configuration wizard is now a single process in Microsoft Exchange Server 2013.
Note:
A hybrid deployment offers organizations the ability to extend the feature-rich experience and administrative control they have with their existing on-premises Microsoft Exchange organization to the cloud. A hybrid deployment provides the seamless look and feel of a single Exchange organization between an on-premises Exchange Server 2013 organization and Exchange Online in Microsoft Office 365. In addition, a hybrid deployment can serve as an intermediate step to moving completely to an Exchange Online organization.
QUESTION 5
You have an Exchange Server 2013 organization.
A user named User1 has a mailbox that is enabled for Unified Messaging (UM).
User1 has nine call answering rules.
When User1 attempts to create a new call answering rule, the user receives an error message.
You need to identify what prevents User1 from creating a call answering rule.
What should you identify?
A. The mailbox of User1 has the CallAnsweringRulesEnabled parameter set to $false
B. The UM mailbox policy of User1 has the AllowCallAnsweringRules parameter set to $false.
C. User1 exceeds the Inbox rules storage quota.
D. User1 has the maximum number of call answering rules allowed.
Answer: D
Explanation:
Call answering rules are created and configured by a voice mail-enabled user using Outlook or Outlook Web App. The rules are stored along with other voice settings in the user’s mailbox.
A total of nine call answering rules can be set up for each UM-enabled mailbox. These rules are independent of the Inbox rules that are set up by users, and don’t take up part of the Inbox rules storage quota for the user.
http://technet.microsoft.com/en-us/library/dd335138%28v=exchg.150%29.aspx
QUESTION 6
You have an Exchange Server 2007 organization.
You deploy a new Exchange Server 2013 organization.
You plan to move all of the mailboxes to the new organization by performing a cross-forest mailbox move.
You need to recommend a solution to meet the following requirements:
– Users must be able to reply successfully to email messages they received before their mailbox moved.
– Users must be able to send email messages to internal mailboxes by using the entries in the nickname cache that existed in Microsoft Outlook before their mailbox moved.
What should you recommend doing before moving the mailboxes?
A. Create a sharing policy and a remote domain.
B. Create an organization relationship and a remote domain.
C. For all of the users in the new organization, add their LegacyExchangeDN value as an x500 proxy address.
D. For all of the users in the new organization, add their LegacyExchangeDN value as an SMTP proxy address.
Answer: C
Explanation:
Problem:
An email is sent and a NDR is generated to the sender showing an X500 address in the recipient field. The cause of this is that Exchange uses the X500 address to route mail internally and once the attributes have been removed from a user object (or a contact was removed) and a mailbox is created for the same user, Exchange creates a new X500 address (it is the same information as before, but the last three characters are randomized to keep them unique within the system).
Resolution:
The simpliest thing to do is add a new custom email address to the user object, paste the old LegacyExchangeDN in the address field, and set the type to X500.
http://russburden.files.wordpress.com/2012/06/customx500.jpg?w=595
QUESTION 7
Drag and Drop Question
Your company has two offices. The offices are located in New York and San Francisco.
You have an Exchange Server 2013 organization that contains two servers. The servers are configured as shown in the following table.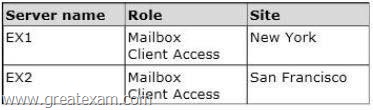
The organization contains four mailbox databases.
The mailbox databases are configured as shown in the following table.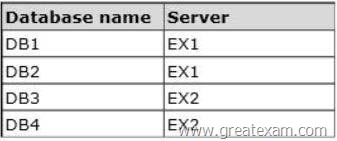
Recently, DB1 went offline because of a disk failure. The disk is restored and DB1 is mounted.
You discover that there are more than 10,000 email messages queued for delivery to DB1.
You need to preserve the messages and perform the following actions:
– Export the messages queued for delivery to a different drive.
– Clear the messages queued for delivery.
– Ensure that the messages queued for delivery to DB1 are delivered while preserving the original message header information.
– Prevent duplicate messages.
Which four actions should you perform in sequence? (To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in the correct order.)
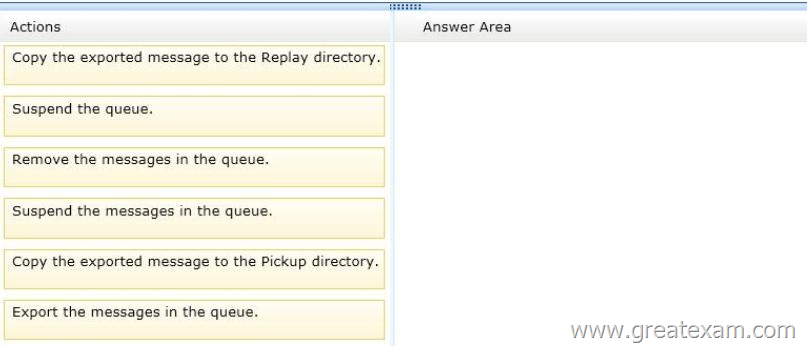
Answer: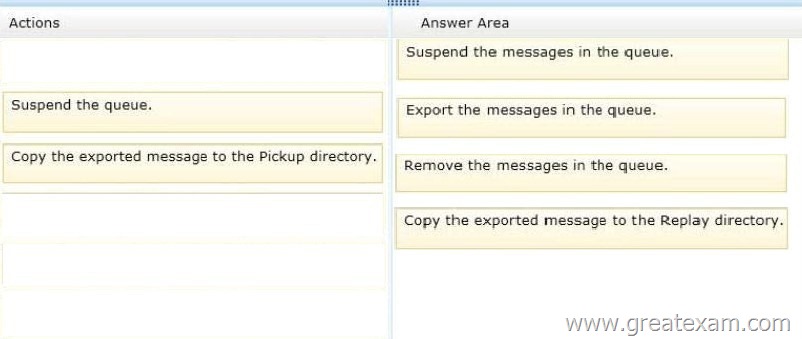
Explanation:
http://technet.microsoft.com/en-us/library/aa998625(v=exchg.150).aspx
http://technet.microsoft.com/en-us/library/bb124230(v=exchg.150).aspx#ReplayMod
http://technet.microsoft.com/en-us/library/aa998625(v=exchg.150).aspx
http://technet.microsoft.com/en-us/library/bb124230%28v=exchg.150%29.aspx
QUESTION 8
You have an Exchange Server 2013 organization.
You successfully migrate the public folders from a previous version of Exchange Server.
You discover that one of the public folder mailboxes almost reached its quota size.
You need to move some of the public folders in the public folder mailbox to another public folder mailbox.
What should you run?
A. Merge PublicFolderMailbox.ps1
B. Set-MailPublicFolder
C. New-PublicFolderMigrationRequest
D. New-PublicFolderMoveRequest
Answer: D
Explanation:
You can either perform a publicfoldermoverequest, or run the splitpublicfoldermailbox.ps1 script.
* If the content of a public folder mailbox begins to exceed your mailbox quotas, you may need to move public folders to a different public folder mailbox. There are a couple ways to do this. To move one or more public folders that don’t contain subfolders, you can use the PublicFolderMoveRequest cmdlets.
* Use the New-PublicFolderMoveRequest cmdlet to begin the process of moving public folder contents between public folder mailboxes. Moving public folders only moves the physical contents of the public folder; it doesn’t change the logical hierarchy. When the move request is completed, you must run the Remove-PublicFolderMoveRequest cmdlet to remove the request or wait until the time specified in the CompletedRequestAgeLimit parameter has passed. The request must be removed before you can run another move request.
QUESTION 9
Hotspot Question
You have an Exchange Server 2013 organization named contoso.com.
Your company, which is named Contoso, Ltd., has a partnership with another company named Fabrikam, Inc.
Fabrikam has an Exchange Server 2013 organization.
Both organizations have a federation trust to the Microsoft Federation Gateway.
You need to ensure that the users at Fabrikam can see the free/busy information of the users at Contoso, including the time, the location, and the subject of appointments.
Which command should you run? (To answer, select the appropriate options in the answer area.)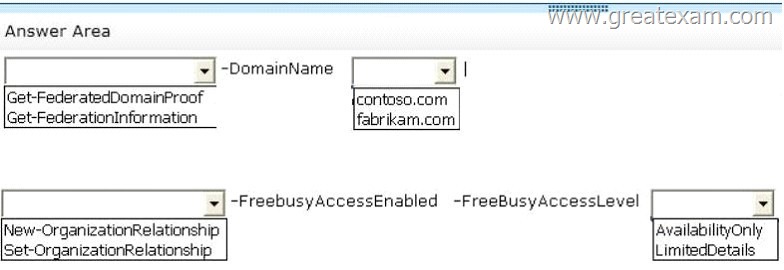
Answer:
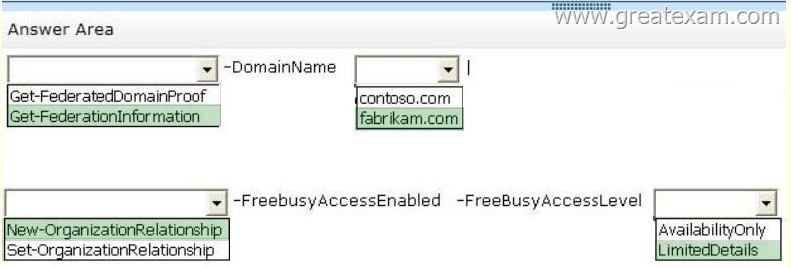
Explanation:
There is no Organization Relationship indicated, only a trust relationship.
Hence, the command should be New-OrganizationRelationship, not Set-Relationship.
Also, the Organization Relationship is created from the domain that wants to do the sharing, so this command is run on Contoso and you would have -DomainName fabrikam.com since that’s the domain you are wanting to share to.
http://technet.microsoft.com/en-us/library/dd351221(v=exchg.150).aspx
The Get-FederationInformation cmdlet retrieves federation information from the domain specified. Results from the cmdlet can be piped to the New-OrganizationRelationship cmdlet to establish an organization relationship with the Exchange organization being queried.
http://technet.microsoft.com/en-us/library/dd351221(v=exchg.150).aspx
An organization relationship enables users in your Exchange organization to share calendar free/busy information as part of federated sharing with other federated Exchange organizations. Federated sharing can be configured between two federated Exchange 2013 organizations or between a federated Exchange 2013 organization and federated Exchange 2010 organizations.
The organization relationship to be created is on Contoso.com, because you create the Organization Relationship on the domain you are sharing from. Hence, you want to get the Federation Information for fabrikam.com.
http://technet.microsoft.com/en-us/library/dd351221%28v=exchg.150%29.aspx
http://technet.microsoft.com/en-us/library/ee332357%28v=exchg.150%29.aspx
The FreeBusyAccessLevel parameter specifies the maximum amount of detail returned to the requesting organization.
You can use the following values:
None No free/busy access
AvailabilityOnly Free/busy access with time only
LimitedDetails Free/busy access with time, subject, and location
Case Study 1: A.Datum (QUESTION 10 ~ QUESTION 19)
Overview
General Overview
A. Datum Corporation is a pet supply company that has stores across North America.
A. Datum has an Exchange Server 2007 organization. A. Datum plans to migrate to Exchange Server 2013.
Physical Locations
A. Datum has five locations. The locations are configured as shown in the following table.
Existing Environment
Network Infrastructure
All of the locations connect to the each other by using a WAN link. The New York, Toronto, and Chicago locations connect directly to the Internet.
All client computers run Windows 7 and Office 2010. All servers run Windows Server 2008.
Active Directory Environment
The network contains an Active Directory domain named adatum.local. Adatum.local is the corporate domain based in the United States. The network contains a domain named Canada.adatum.local. Canada.adatum.local is the domain for the stores in Canada.
Each location is configured as an Active Directory site.
The forest functional level is Windows Server 2008.
The main office and both of the distribution centers each has two domain controllers for their respective domain. All of the other locations have one domain controller for their respective domain. All of the domain controllers are global catalog servers.
Exchange Infrastructure
The main office and the distribution centers each have three servers that have Exchange Server 2007 installed.
The servers have the following configurations:
– Two of the servers have cluster continuous replication (CCR) deployed
– One of the servers has the Client Access server role and the Hub Transport server role installed
Each store contains a server that has Exchange Server 2007 installed. Each server has mailboxes for active users and mailboxes for inactive users. Each server has approximately 50 mailboxes. Remote users access Outlook Web Access by using a namespace of mail.adatum.com, which resolves to the Client Access server in the New York office.
Requirements
Planned Changes
The company plans to implement the following changes:
– Migrate all of the mailboxes in the main office and the distribution centers to Exchange Server 2013.
– Integrate a new telephone system to the Exchange Server 2013 organization.
– Deploy a standalone certification authority (CA) that will be used to issue all of the certificates for the messaging infrastructure.
Technical Requirements
The company identifies the following technical requirements:
– Hardware costs must be minimized whenever possible.
– The impact on end users if a site fails must be minimized.
– Voice mail traffic between the telephone system and the Exchange Server environment must be encrypted.
– Each user must be able to access the internal resources and their mailbox by using a single user account.
Compliance Requirements
After a security review, the company identifies the following compliance requirements for the new Exchange Server environment:
– All administrative changes made to the mailboxes must be tracked.
– The legal department must be able to search for messages in all of the mailboxes.
– Users must be prevented from sending email during an upcoming statutory holiday.
– All store managers must be prevented from permanently deleting email messages from their Inbox.
– All email messages must be archived for a minimum of five years to meet regulatory requirements.
– Management occasionally sends the staff internal memos that contain confidential information, such as sales figures. The memos must be protected so that unauthorized users cannot read the memos and internal users cannot forward the memos to external recipients.
– The users in the research department must be able to send email to anyone in the organization, but only the members of a group named Execs must be able to send email to the research users. All other users must be notified that email sent to the research users will remain undelivered.
QUESTION 10
You need to recommend a solution for the memos.
The solution must meet the compliance requirements.
What should you include in the recommendation?
A. Secure/Multipurpose Internet Mail Extensions (S/MIME)
B. Information Rights Management (IRM)
C. Domain Security
D. Data loss prevention (DLP) policies
Answer: B
Explanation:
* Scenario:
Management occasionally sends the staff internal memos that contain confidential information, such as sales figures. The memos must be protected so that unauthorized users cannot read the memos and internal users cannot forward the memos to external recipients.
* With the IRM features in Exchange 2013, your organization and your users can control the rights recipients have for e-mail. IRM also helps allow or restrict recipient actions such as forwarding a message to other recipients, printing a message or attachment, or extracting message or attachment content by copying and pasting. IRM protection can be applied by users in Microsoft Outlook or Microsoft Office Outlook Web App, or it can be based on your organization’s messaging policies and applied using transport protection rules or Outlook protection rules.
IRM also helps allow or restrict recipient actions such as forwarding a message to other recipients, printing a message or attachment, or extracting message or attachment content by copying and pasting.
http://technet.microsoft.com/en-us/library/dd638140%28v=exchg.150%29.aspx
QUESTION 11
You need to recommend a solution to meet the compliance requirement for the legal department.
What should you include in the recommendation?
A. A retention hold
B. The Discovery Management management role group
C. A litigation hold
D. The Recipient Management management role group
Answer: B
Explanation:
* Scenario:
The legal department must be able to search for messages in all of the mailboxes.
* Administrators or users who are members of the Discovery Management role group can perform searches of mailboxes in the Exchange organization for data that meets specific criteria and can also configure litigation holds on mailboxes.
Discovery management role group is capable of performing legal hold and mailbox search (both roles)
http://technet.microsoft.com/en-us/library/dd351080%28v=exchg.150%29.aspx
QUESTION 12
You are creating a contingency plan to be implemented if the entire New York site fails after Exchange Server 2013 is deployed.
You need to recommend which tasks must be performed to ensure that all of the users can access Outlook Web App from the Chicago site if the New York fails.
Which three actions should you recommend? (Each correct answer presents part of the solution. Choose three.)
A. On the Client Access server in the Chicago site, set the ExternalURL of Outlook Web App to mail.adatum.com.
B. On the Mailbox server in the Chicago site, set the ExternalURL of Outlook Web App to mail.adatum.com.
C. Modify the host (A) record for mail.adatum.com to point to the Client Access server in the Chicago site.
D. On the Client Access server in the Chicago site, set the internal URL of Outlook Web App to mail.adatum.local.
E. Install the mail.adatum.com certificate and private key on the Client Access server in the Chicago site.
Answer: ACE
Explanation:
A: Example: To configure an external URL for Outlook Web App, run the following command in Exchange Management Shell.
Set-OwaVirtualDirectory “<CAS2013>\OWA (Default Web Site)” -ExternalUrl https://mail.contoso.com/OWA
C: Need a new record in the DNS.
E: In Exchange 2013, you can use the Certificate Wizard to request a digital certificate from a certification authority. After you’ve requested a digital certificate, you’ll need to install it on the Client Access server.
Reference: Exchange 2013 Client Access server configuration
QUESTION 13
You need to recommend an auditing solution that meets the compliance requirements.
What should you recommend?
A. Export the mailbox audit log.
B. Run an administrator role group report.
C. Run a non-owner mailbox access report.
D. Export the administrator audit log.
Answer: D
Explanation:
* Scenario:
All administrative changes made to the mailboxes must be tracked.
* You can use administrator audit logging in Microsoft Exchange Server 2013 to log when a user or administrator makes a change in your organization.
By keeping a log of the changes, you can trace changes to the person who made the change, augment your change logs with detailed records of the change as it was implemented, comply with regulatory requirements and requests for discovery, and more.
http://technet.microsoft.com/en-us/library/dd335144%28v=exchg.150%29.aspx
QUESTION 14
You deploy a new certificate to a Client Access server.
You test the new certificate by using Outlook Anywhere from the Internet.
The test generates certificate errors.
You need to prevent the errors from reoccurring.
To which two stores should you add the root CA certificate? (Each correct answer presents part of the solution. Choose two.)
A. the personal store on the client computers
B. the personal store on the Client Access server
C. the personal store on the Mailbox servers
D. the Trusted Root Certification Authorities store on the client computers
E. the Trusted Root Certification Authorities store on the Client Access server
F. the Trusted Root Certification Authorities store on the Mailbox servers
Answer: DE
Explanation:
D: Outlook Anywhere won’t work with a self-signed certificate on the Client Access server. Self-signed certificates must be manually copied to the trusted root certificate store on the client computer or mobile device. When a client connects to a server over SSL and the server presents a self-signed certificate, the client will be prompted to verify that the certificate was issued by a trusted authority. The client must explicitly trust the issuing authority. If the client confirms the trust, then SSL communications can continue.
E: If you are providing external access to Autodiscover by using Outlook Anywhere you must install a valid SSL certificate on the Client Access server.
http://technet.microsoft.com/en-us/library/cc754841.aspx
http://technet.microsoft.com/en-us/library/dd351044%28v=exchg.150%29.aspx
http://technet.microsoft.com/en-us/library/cc700805.aspx#XSLTsection126121120120
QUESTION 15
You need to recommend a solution to ensure that the store managers meet the compliance requirements.
What should you include in the recommendation?
A. Retention tags and retention policies
B. Deleted item retention
C. An in-place hold
D. Personal archives
Answer: C
Explanation:
* Scenario:
All store managers must be prevented from permanently deleting email messages from their Inbox.
* In Exchange 2013, you can use In-Place Hold to accomplish the following goals:
Place user mailboxes on hold and preserve mailbox items immutably Preserve mailbox items deleted by users or automatic deletion processes such as MRM
* Preserve items indefinitely or for a specific duration Etc.
http://technet.microsoft.com/en-us/library/ff637980%28v=exchg.150%29.aspx
QUESTION 16
You need to recommend a solution to ensure that during the planned migrations, all Autodiscover requests are processed by the Exchange Server 2013 Client Access servers.
What should you recommend?
A. On the Exchange Server 2007 Client Access servers, modify the AutodiscoverServiceInternalURI.
B. On the Exchange Server 2007 Client Access servers, modify the ExternalURL value of the Autodiscover virtual directory.
C. On the Exchange Server 2013 Client Access servers, modify the ExternalURL value of the Autodiscover virtual directory.
D. on the Exchange Server 2013 Client Access servers, modify the AutodiscoverServiceInternalURI.
Answer: A
Explanation:
The Exchange Server 2007 Client Access servers must be configured to use the Exchange Server 2013 Client Access server. We do this by setting the AutodiscoverServiceInternalURI property.
QUESTION 17
You need to recommend a solution for the voice mail traffic.
The solution must meet the technical requirements.
Which two configurations should you include in the recommendation? (Each correct answer presents part of the solution. Choose two.)
A. A dial plan.
B. a server certificate
C. a transport rule
D. a data loss prevention (DLP) policy
E. a call answering rule
Answer: AB
Explanation:
* Scenario:
Voice mail traffic between the telephone system and the Exchange Server environment must be encrypted.
A: Use the EAC to configure Protected Voice Mail from authenticated callers In the EAC, navigate to Unified Messaging > UM dial plans. In the list view, select the UM dial plan you want to modify, and then click Edit . On the UM Dial Plan page, under UM Mailbox Policies, select the UM mailbox policy you want to manage, and then click Edit .
On the UM Mailbox Policy page > Protected voice mail, under Protect voice message from authenticated callers, select one of the following options:
Click Save.
B:* In on-premises and hybrid deployments, you can configure a Client Access and Mailbox server to use mutual Transport Layer Security (mutual TLS) to encrypt the SIP and RTP traffic sent and received from other devices and servers. When you configure the dial plan to use SIP secured mode, only the SIP signaling traffic will be encrypted, and the RTP media channels will still use TCP, which isn’t encrypted. However, when you configure the dial plan to use Secured mode, both the SIP signaling traffic and the RTP media channels are encrypted. An encrypted signaling media channel that uses Secure Realtime Transport Protocol (SRTP) also uses mutual TLS to encrypt the VoIP data.
* When you’re deploying Transport Layer Security (TLS) with UM, the certificates that are used on the Client Access server and the Mailbox server both must contain the local computer’s fully qualified domain name (FQDN) in the certificate’s Subject Name. To work around this issue, use a public certificate and import the certificate on all Client Access and Mailbox servers, any VoIP gateways, IP PBXs, and all the Lync servers.
http://technet.microsoft.com/en-us/library/bb676409(v=exchg.150).aspx
QUESTION 18
Drag and Drop Question
You need to recommend a solution to meet the compliance requirements for the research department and the statutory holidays.
What should you recommend configuring?
To answer, drag the appropriate object to the correct location in the answer area. Each object may be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.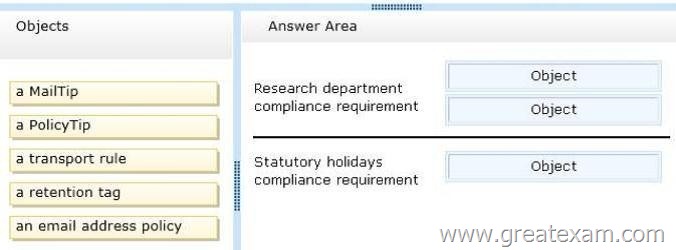
Answer: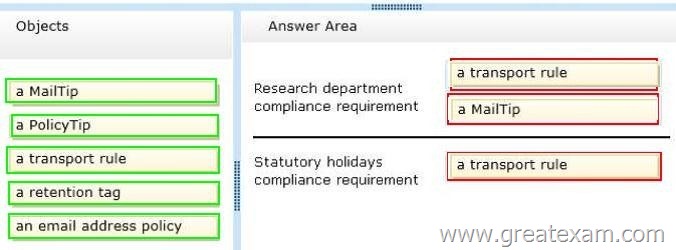
QUESTION 19
Hotspot Question
You need to recommend a database availability group (DAG) design that meets the technical requirements.
Which DAG design should you recommend? To answer, select the appropriate design in the answer area.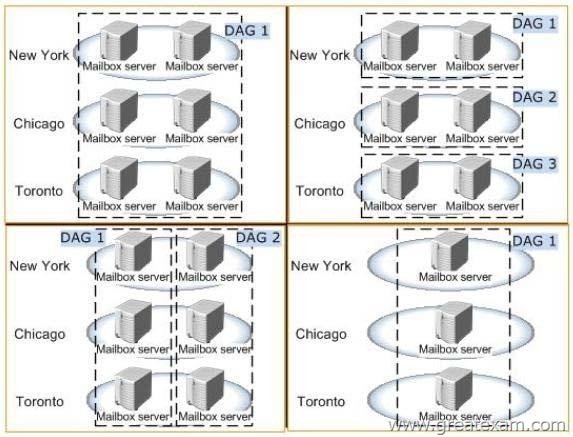
Answer: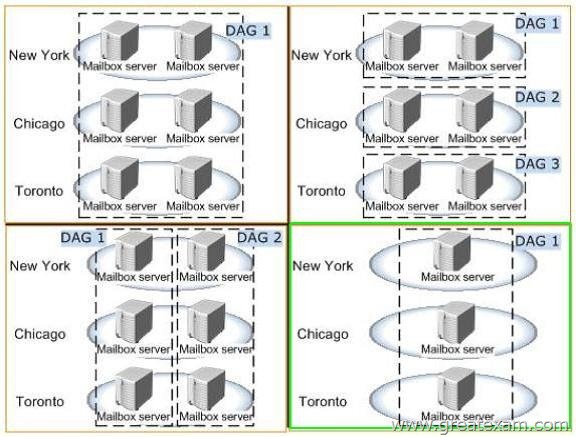
Explanation:
http://technet.microsoft.com/en-us/library/dd979802(v=exchg.150).aspx
Case Study 2: Contoso Ltd (QUESTION 20 ~ QUESTION 27)
Overview General
Overview
Contoso, Ltd., is an aerospace engineering company that manufactures jet engine parts for various industries and government agencies. Contoso has an Exchange Server 2013 organization.
A partner company named Tailspin Toys has an Exchange Server 2010 organization.
Physical Locations
Contoso has two offices. The offices are located in Montreal and Chicago.
Each office contains a data center:
– The Montreal and Chicago offices connect to each other by using a direct WAN link.
– All connections to the Internet are routed through the Montreal office.
– Most of Contoso’s employees work from the Montreal office.
Existing Environment
The network of Contoso is configured as shown in the exhibit. (Click the Exhibit button.)
The network of Contoso contains the following components:
– Client computers that run either Microsoft Outlook 2007 or Outlook 2010.
– Users who have a primary SMTP address that uses the contoso.com suffix.
– A retention policy that retains all email messages for 580 days and is associated to all users.
– Six servers that have Exchange Server installed.
The servers are configured as shown in the following table.
A data availability group (DAG) named DAG1 that contains all of the mailbox servers. EX5 is configured as the witness server for DAG1. A file server in the Chicago office is configured as an alternate witness server. DAG1 has Datacenter Activation Coordination (DAC) mode enabled.
Requirements
Planned Changes
Contoso plans to implement the following changes:
– Implement an organization relationship between Contoso and Tailspin Toys.
– Move the mailboxes of all the members of the sales department to Office 365.
– Evaluate Unified Messaging (UM) by conducting a small pilot in the Montreal office.
Security Requirements
Contoso identifies the following security requirements:
– Ensure that the data in the Exchange Server databases cannot be read if a hard disk is stolen.
– Prevent temporary employees from executing a Reply All or a Forward of any email messages they receive.
– Prevent temporary contractors from changing the configurations of the user accounts for the users in the research and development department.
– Ensure that all of the connections to Outlook Web App from the Internet use Extensible Authentication Protocol (EAP) protocols and Transport Layer Security (TLS) protocols.
– Secure all of the email messages from the users at Tailspin Toys to the Contoso users. Ensure that all of the messages can be secured if the certificates at Tailspin Toys are issued by a trusted third-party certification authority (CA).
Auditing Requirements
Contoso identifies the following requirements for auditing mailboxes:
– The manager of the legal department must receive a daily report by email that contains a record of all the eDiscovery mailbox searches.
– Any access to a mailbox by a service account must be excluded from the daily report.
Compliance Requirements
All of the email messages in the Sent Items folder of each user in the marketing department of Contoso must be deleted automatically after 365 days.
Office 365 Coexistence Requirements
Contoso identifies the following Office 365 coexistence requirements:
– Office 365 users must be able to access their mailbox by using their Active Directory user account in Contoso.
– On-premises users must be able to share free/busy information and calendar information with the Office 365 users.
QUESTION 20
You are evaluating the implementation of the organization relationship.
You need to recommend which tasks must be performed to ensure that the Contoso users can view the Out of Office message of the Tailspin Toys users before the Contoso users send a message to the Tailspin Toys users.
What should you recommend doing before implementing the organization relationship?
A. Create a Policy Tip.
B. Upgrade all of the client computers to Outlook 2010.
C. Create a MailTip.
D. Publish the Autodiscover service of Tailspin Toys.
E. Create a remote domain.
Answer: B
Explanation:
* Scenario:
Implement an organization relationship between Contoso and Tailspin Toys.
Microsoft Outlook 2007 is a legacy product. Mail tips not supported.
http://blogs.technet.com/b/exchange/archive/2009/04/28/introducing-mailtips.aspx
GreatExam gives the latest, authoritative and complete 70-342 braindumps for 70-342 exam, because of that, all of our candidates pass 70-342 certification without any problem. The biggest feature is the regular update of 70-342 PDF and VCE, which keeps our candidates’ knowledge up to date and ensures their 70-342 exam success.